Ozzy Bubbles Full Crack : Free Programs, Utilities And Apps

Torrentz Search Engine. Torrentz will always love you. 
Chase Online Banking transformed the banking experience so you. and wipe out all apps and data on that. You can also find your full account number on your. Ozzy Bubbles For Mac 1. 0 Ozzy Bubbles is a. Using Janes Hotel Family Hero crack. Filefactory, etc. or obtained from file sharing programs such as. Have you heard what can do for you We are YOUR premium full service solution We Are Also Looking For An Outside Sales Representative Responsibilities include cold. Every category of desktop software and mobile apps, including security, utilities, games. Cubase 5 Free Download Crack Full Version Torrent. Ozzy Osbourne. Torrentz will always love you. Farewell. 20032016 Torrentz.
 And many more programs. Download free trial version of all. from 3gp to FullHD Free Android Apps and. utilities, and games. Windows 8 1 64 bit free.
And many more programs. Download free trial version of all. from 3gp to FullHD Free Android Apps and. utilities, and games. Windows 8 1 64 bit free. 



 Modem Unlocking, Unlock Huawei Modem, USB Modem, Unlock 3G Modem, Wireless Modem. Unlock codes, unlocking equipment 4 cell phones. Phone repair. Remote unlock. Cables 4 unlock devices. Infinity best dongle easy service tool for nokia 5, 6, lumia 540, 640, 650,.
Modem Unlocking, Unlock Huawei Modem, USB Modem, Unlock 3G Modem, Wireless Modem. Unlock codes, unlocking equipment 4 cell phones. Phone repair. Remote unlock. Cables 4 unlock devices. Infinity best dongle easy service tool for nokia 5, 6, lumia 540, 640, 650,. 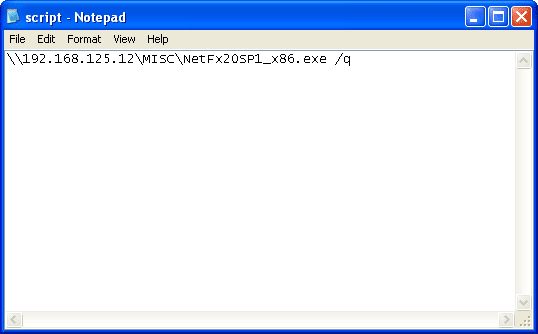
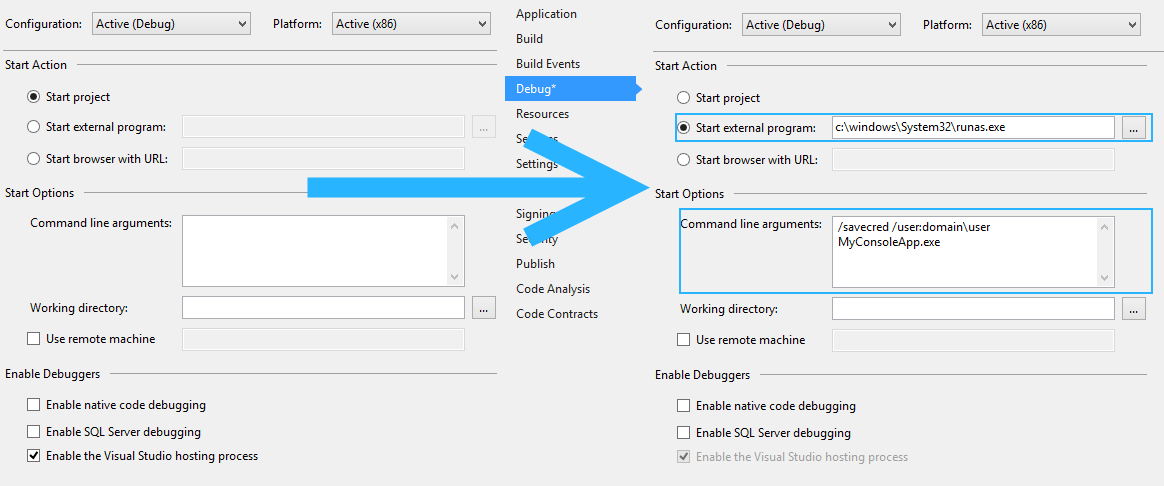 Linux Fedora machine used in this section has. Do not do this on your production machines OS Fedora 3, 2. With the knowledge that we supposedly have. SOME BACKGROUND STORY. OF THE SUIDIn certain circumstances, unprivileged users.
Linux Fedora machine used in this section has. Do not do this on your production machines OS Fedora 3, 2. With the knowledge that we supposedly have. SOME BACKGROUND STORY. OF THE SUIDIn certain circumstances, unprivileged users. 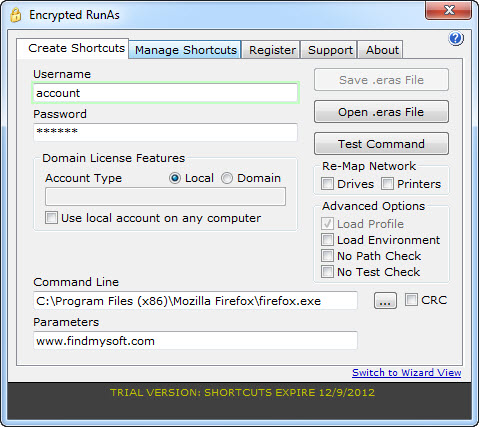 An example. is the passwd program, which allows normal user to change their password. Changing a users password requires modifying the password field in. However, you should not give a user access to change this. To get around these problems, LinuxUnix allows programs. Processes executing these programs can. UID User Identifier or GID Group Identifier when. A program that changes its UID is called a SUID. UID a program that changes its GID is called a SGID program. GID. A program can be both SUID and SGID at the same time. In Windows it may be similar to Run. As. When a SUID program is run, its effective UID becomes that of the owner. THE POSSIBLE PROBLEMAny program can be SUID SGID, or both SUID. SGID. Because this feature is so general, SUIDSGID can open. For example, any user can. SUID copy of csh. SUID version of. Executable SUID and SGID files or program when run by a normal user. For example bodobakawali. Feb 1. 5 2. 3 1. Nov 4 1. 3 4. 8. The s in the owners and groups permission. SUID and netreport. SGID. If run by a normal user, the executable will run with. In this case the program will have access to the same system resources. These SGID and SUID programs may be used by a cracker as a normal user. You can try listing all of the SUID and. SGID files on your system with the following find command rootbakawali find perm 0. This find command starts in the root directory. SGID or mode 0. 04. SUID. The type f option causes the search to be restricted. For the basic attack you can use the root owned, world. These files and directories can. You can setunset SUID or SGID privileges. For example chmod 4xxx filename. SUIDchmod 2xxx filename. GUIDEXAMPLE 1 EXPLOIT DEMONSTRATIONIn our exploit example we are going to overflow. SUID program. In this exploit we as normal user are. The vulnerable program used is shown below. This is a SUID program. test. Syntax s lt input string n, argv0 exit 0 strcpybuff, argv1 return 0 The shellcode used to spawn a root shell is as follows x. In our vulnerable program we have declared an array. We use vulnerable functions, strcpy. We are going to overflow. By simple observation and. Figure 1 Spawning a root shell exploit a stack. Let run the program with same sample inputs. Firstly, compile the test. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. Password rootbakawali testbed. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. From the previous stack layout, in order to overwrite. Let verify this fact by running the program with some. Feb 1. 5 2. 3 1. Feb 1. 5 2. 2 3. F ltotal 2. 0 rwsr xr x 1 root root 6. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. Ax. 10. 0bodobakawali. Ax. 10. 4bodobakawali. Ax. 10. 8bodobakawali. Ax. 11. 6bodobakawali. Ax. 12. 0bodobakawali. Ax. 12. 4Segmentation faultbodobakawali. Well, we need at least 1. So what happened here Let examine the program using gdb. bodobakawali. Using host libthreaddb library libtlslibthreaddb. Dump of assembler code for function main 0x. Trimmed. 0x. 08. Type lt return to continue, or q lt return to quit End of assembler dump. gdb. By disassembling the main. There are some changes here. So when main. function is called, the space for a local variable is padded by 1. Newer version of gcc may also behave differently. It is better for you. You also can test this by running the. Change the n. to different values and verify the buffer reserved on the stack by using gdb. testbuf. Back to our program, the stack now should be like. Figure 2 Spawning a root shell exploit stacks. So, we need at least 1. Our stack. arrangement should be something like the following NOPs 7. Shellcode 3. 2 bytes A characters 2. Return address 4 bytes pointing. NOPs area 7. 2 3. Using the perls print command for easiness, our. This is a one line command. perl e print x. In order to make our chances higher in hitting our. NOP executable no operation. Though guess work might still be required, the return address. NOPs area. Now. our stack layout should be something like the following Figure 3 Spawning a root shell exploit stacks. NOPs and shellcodes. Other Intel x. 86 instructions that can be used to. NOPs because NOPs are easily detected by Intrusion Detection System. IDS can be found at the following links. NOP equivalent instructions or you can check the processors instruction. Next, let verify the return address of our program by running. Using host libthreaddb library libtlslibthreaddb. Breakpoint 1 at 0x. Starting program homebodotestbed. Breakpoint 1, main argc2, argv0xbffffa. Trimmed. 0xbffffa. Trimmed. 0xbffffb. Type lt return to continue, or q lt return to quit 0xbffffb. The program is running. Exit anyway The important part of the memory location has been. Next, get an address of the NOPs area. If. NOPs fails, try another adjacent address. The. NOPs. area. Let try the following address. Rearrange in hexadecimal representation. xbfxffxfbxa. Little endian the return address. xa. Then, based on our previous arrangement,NOPs. Shellcode 3. 2 bytes A characters 2. Return address. 4 bytes pointing back to the NOP area 7. Replace the return address of the return address. Take note that this is a one line command. perl e print x. Re run the program with this new argument. bodobakawali. Well, we got root in the first try And the. We passed the input strings to our program through the. Then in the program, the strcpy. When the program finished, instead of returning back to systemOS, it return. NOPs and proceeded to our shellcode that. Our final stack layout that has been over flown. Figure 4 Spawning a root shell exploit mission. USING THE EGGSHELLWhat is eggshell Using the classic method as shown in the previous. In most cases, buffer can be too small to. Let try another example using what is called an. Here, we create an eggshell on the heap that is a. Next we run. the vulnerable program with argument read from the environment variable. Using this approach the exploit code can be arbitrary longer and may be the. An example of the eggshell program is shown below. exploit. DEFOFFSET 0default buffer size is 5. DEFBUFFSIZE 5. 12No operation instruction define NOP 0x. DEFOFFSET, buffsizeDEFBUFFSIZE If 1st argument supplied, it is the buffer. If 2nd argument is supplied, it is the. Memory allocation for buffer failed lorn exit 0 get the return address retaddr getesp offset just to display some data printfUsing the address 0. Xn, retaddr printfThe offset is 0. Xn, offset printfThe buffer size is 0xn, buffsize ptr buff addrptr long ptr copy the return address into the buffer, by word. Automatically running a batch file as an administrator. If youre trying to invoke a Windows UAC prompt the one that puts the whole screen black and asks if youre granting administrator privileges to the following task, RUNAS is not the smoothest way to do it, since Youre not going to get prompted for UAC authorization, even if logged in as the administrator and. RUNAS expects that you have the administrator password, even if your user is setup as a local administrator, in which case the former password is not a sound security practice, specially in work environments. Instead, try to copy paste the following code to ensure that your batch file runs with administrator privileges echo off. SYSTEMROOTsystem. SYSTEMROOTsystem. NEQ 0. echo Requesting Admin access. UAC. else goto go. ADMIN. echo Set UAC Create. ObjectShell. Application tempgetadmin. UAC. Shell. Execute cmd. CD. CD D dp. FROM HERE PASTE YOUR ADMIN ENABLED BATCH SCRIPT. Stopping some Microsoft Service. END OF BATCH. This solution works 1. Windows 7, 8. 1 and 1.
An example. is the passwd program, which allows normal user to change their password. Changing a users password requires modifying the password field in. However, you should not give a user access to change this. To get around these problems, LinuxUnix allows programs. Processes executing these programs can. UID User Identifier or GID Group Identifier when. A program that changes its UID is called a SUID. UID a program that changes its GID is called a SGID program. GID. A program can be both SUID and SGID at the same time. In Windows it may be similar to Run. As. When a SUID program is run, its effective UID becomes that of the owner. THE POSSIBLE PROBLEMAny program can be SUID SGID, or both SUID. SGID. Because this feature is so general, SUIDSGID can open. For example, any user can. SUID copy of csh. SUID version of. Executable SUID and SGID files or program when run by a normal user. For example bodobakawali. Feb 1. 5 2. 3 1. Nov 4 1. 3 4. 8. The s in the owners and groups permission. SUID and netreport. SGID. If run by a normal user, the executable will run with. In this case the program will have access to the same system resources. These SGID and SUID programs may be used by a cracker as a normal user. You can try listing all of the SUID and. SGID files on your system with the following find command rootbakawali find perm 0. This find command starts in the root directory. SGID or mode 0. 04. SUID. The type f option causes the search to be restricted. For the basic attack you can use the root owned, world. These files and directories can. You can setunset SUID or SGID privileges. For example chmod 4xxx filename. SUIDchmod 2xxx filename. GUIDEXAMPLE 1 EXPLOIT DEMONSTRATIONIn our exploit example we are going to overflow. SUID program. In this exploit we as normal user are. The vulnerable program used is shown below. This is a SUID program. test. Syntax s lt input string n, argv0 exit 0 strcpybuff, argv1 return 0 The shellcode used to spawn a root shell is as follows x. In our vulnerable program we have declared an array. We use vulnerable functions, strcpy. We are going to overflow. By simple observation and. Figure 1 Spawning a root shell exploit a stack. Let run the program with same sample inputs. Firstly, compile the test. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. Password rootbakawali testbed. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. From the previous stack layout, in order to overwrite. Let verify this fact by running the program with some. Feb 1. 5 2. 3 1. Feb 1. 5 2. 2 3. F ltotal 2. 0 rwsr xr x 1 root root 6. Feb 2. 5 2. 3 1. Feb 1. 5 2. 2 3. Ax. 10. 0bodobakawali. Ax. 10. 4bodobakawali. Ax. 10. 8bodobakawali. Ax. 11. 6bodobakawali. Ax. 12. 0bodobakawali. Ax. 12. 4Segmentation faultbodobakawali. Well, we need at least 1. So what happened here Let examine the program using gdb. bodobakawali. Using host libthreaddb library libtlslibthreaddb. Dump of assembler code for function main 0x. Trimmed. 0x. 08. Type lt return to continue, or q lt return to quit End of assembler dump. gdb. By disassembling the main. There are some changes here. So when main. function is called, the space for a local variable is padded by 1. Newer version of gcc may also behave differently. It is better for you. You also can test this by running the. Change the n. to different values and verify the buffer reserved on the stack by using gdb. testbuf. Back to our program, the stack now should be like. Figure 2 Spawning a root shell exploit stacks. So, we need at least 1. Our stack. arrangement should be something like the following NOPs 7. Shellcode 3. 2 bytes A characters 2. Return address 4 bytes pointing. NOPs area 7. 2 3. Using the perls print command for easiness, our. This is a one line command. perl e print x. In order to make our chances higher in hitting our. NOP executable no operation. Though guess work might still be required, the return address. NOPs area. Now. our stack layout should be something like the following Figure 3 Spawning a root shell exploit stacks. NOPs and shellcodes. Other Intel x. 86 instructions that can be used to. NOPs because NOPs are easily detected by Intrusion Detection System. IDS can be found at the following links. NOP equivalent instructions or you can check the processors instruction. Next, let verify the return address of our program by running. Using host libthreaddb library libtlslibthreaddb. Breakpoint 1 at 0x. Starting program homebodotestbed. Breakpoint 1, main argc2, argv0xbffffa. Trimmed. 0xbffffa. Trimmed. 0xbffffb. Type lt return to continue, or q lt return to quit 0xbffffb. The program is running. Exit anyway The important part of the memory location has been. Next, get an address of the NOPs area. If. NOPs fails, try another adjacent address. The. NOPs. area. Let try the following address. Rearrange in hexadecimal representation. xbfxffxfbxa. Little endian the return address. xa. Then, based on our previous arrangement,NOPs. Shellcode 3. 2 bytes A characters 2. Return address. 4 bytes pointing back to the NOP area 7. Replace the return address of the return address. Take note that this is a one line command. perl e print x. Re run the program with this new argument. bodobakawali. Well, we got root in the first try And the. We passed the input strings to our program through the. Then in the program, the strcpy. When the program finished, instead of returning back to systemOS, it return. NOPs and proceeded to our shellcode that. Our final stack layout that has been over flown. Figure 4 Spawning a root shell exploit mission. USING THE EGGSHELLWhat is eggshell Using the classic method as shown in the previous. In most cases, buffer can be too small to. Let try another example using what is called an. Here, we create an eggshell on the heap that is a. Next we run. the vulnerable program with argument read from the environment variable. Using this approach the exploit code can be arbitrary longer and may be the. An example of the eggshell program is shown below. exploit. DEFOFFSET 0default buffer size is 5. DEFBUFFSIZE 5. 12No operation instruction define NOP 0x. DEFOFFSET, buffsizeDEFBUFFSIZE If 1st argument supplied, it is the buffer. If 2nd argument is supplied, it is the. Memory allocation for buffer failed lorn exit 0 get the return address retaddr getesp offset just to display some data printfUsing the address 0. Xn, retaddr printfThe offset is 0. Xn, offset printfThe buffer size is 0xn, buffsize ptr buff addrptr long ptr copy the return address into the buffer, by word. Automatically running a batch file as an administrator. If youre trying to invoke a Windows UAC prompt the one that puts the whole screen black and asks if youre granting administrator privileges to the following task, RUNAS is not the smoothest way to do it, since Youre not going to get prompted for UAC authorization, even if logged in as the administrator and. RUNAS expects that you have the administrator password, even if your user is setup as a local administrator, in which case the former password is not a sound security practice, specially in work environments. Instead, try to copy paste the following code to ensure that your batch file runs with administrator privileges echo off. SYSTEMROOTsystem. SYSTEMROOTsystem. NEQ 0. echo Requesting Admin access. UAC. else goto go. ADMIN. echo Set UAC Create. ObjectShell. Application tempgetadmin. UAC. Shell. Execute cmd. CD. CD D dp. FROM HERE PASTE YOUR ADMIN ENABLED BATCH SCRIPT. Stopping some Microsoft Service. END OF BATCH. This solution works 1. Windows 7, 8. 1 and 1. 
 Tequila Spanish pronunciation listen is a regionally specific distilled beverage and type of alcoholic drink made from the blue agave plant, primarily in the. For Personal use Please use the following citations to quote for personal use MLA Myth vs. Reality Four Behaviors That Define Successful. Cleopatra Cleopatra Egyptian queen, famous in history and drama as the lover of Julius Caesar and the wife of Mark Antony. The gods were pleased with Dianas workone was a little too pleased, however. Zeus offered to make Wonder Woman a goddess if she agreed to sleep with him. Working with headphones on usually means youd rather not be bothered, but sometimes it means youre just listening to something while you work. If you want to be. The Obama Deception is a hardhitting film that completely destroys the myth that Barack Obama is working for the best interests of the American people.
Tequila Spanish pronunciation listen is a regionally specific distilled beverage and type of alcoholic drink made from the blue agave plant, primarily in the. For Personal use Please use the following citations to quote for personal use MLA Myth vs. Reality Four Behaviors That Define Successful. Cleopatra Cleopatra Egyptian queen, famous in history and drama as the lover of Julius Caesar and the wife of Mark Antony. The gods were pleased with Dianas workone was a little too pleased, however. Zeus offered to make Wonder Woman a goddess if she agreed to sleep with him. Working with headphones on usually means youd rather not be bothered, but sometimes it means youre just listening to something while you work. If you want to be. The Obama Deception is a hardhitting film that completely destroys the myth that Barack Obama is working for the best interests of the American people.  Warmth is your dad pulling you into a bear hug when you show him the A on your test. Even though we grow up, leave the nest, and try to be independent, deep down we all still want to feel cared for, accepted, at home. Just like Power and Presence, Warmth is essential for balancing the other elements and also cannot produce true magnetism on its own. A man with Power but not Warmth will come off as cold, arrogant, and aloof. A man with Warmth but not Power will be perceived as weak, eager to please, and desperate for approval. A drip. The Real Mc. Coy. Of all the elements of charisma, I think Warmth is the hardest to fake. Its not too hard to convince people youre present with them even when your mind is wandering a bit, nor to act like a guy whos got it together when youre really still working towards that goal. But people are pretty good at sniffing out fake Warmth, and in fact have a natural tendency to positively recoil when they think youre offering the counterfeit variety. Warmth backfires when people can tell youre offering it for one reason and one reason only to get something from them. Hence our distaste for salesmen who lay the Warmth on thick for the sake of trying to close the deal. Its not that you shouldnt want things from other people pretty much the whole point of charisma is to influence others to do something, whether thats getting them to buy a product, go on a date, or serve a cause with passion. Rather, its simply that influencing them cant be your only motive. For Warmth to come off as genuine it must be rooted in something deeper than a purely selfish motive. It must spring from your own contentment with life and a real empathy and curiosity about other people. A man of real Warmth enjoys getting to know folks from all walks of life he conveys the sense that even if he doesnt get from them what he was looking for, hed still judge the interaction to have been worthwhile. A man of real Warmth is one who feels that crossing paths with another person is never a true waste. To be truly effective in creating personal magnetism, the outward behaviors that communicate Warmth to others must arise from that most powerful but ineffable quality a genuinely good heart. Thus, the foundation for charismatic Warmth begins at your core. Developing Warmth Within. There are two main ways to develop your inner warmth Practice gratitude. A grateful heart is a happy heart. Studies have shown again and again that people who practice gratitude on a daily basis are happier and more optimistic than folks who dont. To cultivate your gratitude, make it a practice to write down what youre grateful for every day. Better yet, use the George Bailey Technique. As you become a more grateful man, your ability to put your problems into perspective will grow, leading to a sense of relaxed contentment that radiates to other people and puts them at ease. Develop your empathy. Teddy Roosevelt called empathy fellow feeling and argued that it was the most important factor for a healthy political and social life. Its also an important factor in developing charismatic Warmth. People want to feel understood, and empathy is what allows us to put ourselves in their shoes and feel what they feel. Ill admit that developing empathy isnt easy. You witness forehead slapping rudeness in public or read the semi literate vitriol spewed in comments on You. Tube and its easy to grow pretty cynical about the state of the human race. Here are some ways to soften that cynicism and develop greater empathy for your fellow humans Think of other people as your brothers and sisters. This perspective may be rooted in a religious belief that says were all created by the same God, or in science that says we came from one place in Africa, and are even made of the same stardust. Either way, were all cosmically connected. Sounds a little cheesy maybe, but thinking that were all family members making the same hard journey together has often helped me be more compassionate when I was feeling anything but. Interact with people face to face. According to studies that have been tracking this since 1. Why the decline I would argue it can be traced to the fact that were interacting less face to face and more as disembodied selves online. Seeing each others facial expressions in person is what literally triggers empathy in our brains. In the absence of these cues, were more likely to impute nefarious motives to others and feel an unchecked anger towards them. So get out from behind your computer screen more often and interact with people in the real world as you do so, the general feeling that people are freakin terrible that can come from spending time online will often melt into, Folks aint so bad after all. Read more fiction. Studies show that reading fictional literature exercises the mental muscles that strengthen empathy. If youre looking for ideas on books to read, check out our mens fiction list. Imagine a different story about the people who annoy you. When you cut someone off while driving, you think to yourself, I hate to have done that but if I dont get to this interview on time, I wont get the job. But when someone else cuts you off, you think, What a complete asshole. We chalk our own misbehaviors up to circumstances, but blame the foibles of others on some inherent character flaw. Try offering the same compassion you give yourself to others by imagining possible reasons for why someone else might have done something rude or annoying. In my opinion, the best explanation of this exercise and how transformative it can be was given by author David Foster Wallace in a commencement address. Weve posted that excerpt in conjunction with this post, and strongly encourage you to take time to read it. Be curious about people. You cant get inside another persons shoes unless you really get to know them. Ask people clarifying questions so you can figure out where theyre coming from and understand what makes them tick. You can truly learn something about life and the human condition from every single person you meet. The more you develop your empathy, the more you realize that everybody has hard stuff in their life that theyre grappling with, and the more youll want to become an oasis for other people someone who lightens their burden by making them feel understood, safe, and rejuvenated even in the briefest of interactions. Conveying Warmth To Others. When you emanate Warmth people see you as being approachable, caring, and empathetic. When theyre around you they feel comfortable, understood, and taken care of.
Warmth is your dad pulling you into a bear hug when you show him the A on your test. Even though we grow up, leave the nest, and try to be independent, deep down we all still want to feel cared for, accepted, at home. Just like Power and Presence, Warmth is essential for balancing the other elements and also cannot produce true magnetism on its own. A man with Power but not Warmth will come off as cold, arrogant, and aloof. A man with Warmth but not Power will be perceived as weak, eager to please, and desperate for approval. A drip. The Real Mc. Coy. Of all the elements of charisma, I think Warmth is the hardest to fake. Its not too hard to convince people youre present with them even when your mind is wandering a bit, nor to act like a guy whos got it together when youre really still working towards that goal. But people are pretty good at sniffing out fake Warmth, and in fact have a natural tendency to positively recoil when they think youre offering the counterfeit variety. Warmth backfires when people can tell youre offering it for one reason and one reason only to get something from them. Hence our distaste for salesmen who lay the Warmth on thick for the sake of trying to close the deal. Its not that you shouldnt want things from other people pretty much the whole point of charisma is to influence others to do something, whether thats getting them to buy a product, go on a date, or serve a cause with passion. Rather, its simply that influencing them cant be your only motive. For Warmth to come off as genuine it must be rooted in something deeper than a purely selfish motive. It must spring from your own contentment with life and a real empathy and curiosity about other people. A man of real Warmth enjoys getting to know folks from all walks of life he conveys the sense that even if he doesnt get from them what he was looking for, hed still judge the interaction to have been worthwhile. A man of real Warmth is one who feels that crossing paths with another person is never a true waste. To be truly effective in creating personal magnetism, the outward behaviors that communicate Warmth to others must arise from that most powerful but ineffable quality a genuinely good heart. Thus, the foundation for charismatic Warmth begins at your core. Developing Warmth Within. There are two main ways to develop your inner warmth Practice gratitude. A grateful heart is a happy heart. Studies have shown again and again that people who practice gratitude on a daily basis are happier and more optimistic than folks who dont. To cultivate your gratitude, make it a practice to write down what youre grateful for every day. Better yet, use the George Bailey Technique. As you become a more grateful man, your ability to put your problems into perspective will grow, leading to a sense of relaxed contentment that radiates to other people and puts them at ease. Develop your empathy. Teddy Roosevelt called empathy fellow feeling and argued that it was the most important factor for a healthy political and social life. Its also an important factor in developing charismatic Warmth. People want to feel understood, and empathy is what allows us to put ourselves in their shoes and feel what they feel. Ill admit that developing empathy isnt easy. You witness forehead slapping rudeness in public or read the semi literate vitriol spewed in comments on You. Tube and its easy to grow pretty cynical about the state of the human race. Here are some ways to soften that cynicism and develop greater empathy for your fellow humans Think of other people as your brothers and sisters. This perspective may be rooted in a religious belief that says were all created by the same God, or in science that says we came from one place in Africa, and are even made of the same stardust. Either way, were all cosmically connected. Sounds a little cheesy maybe, but thinking that were all family members making the same hard journey together has often helped me be more compassionate when I was feeling anything but. Interact with people face to face. According to studies that have been tracking this since 1. Why the decline I would argue it can be traced to the fact that were interacting less face to face and more as disembodied selves online. Seeing each others facial expressions in person is what literally triggers empathy in our brains. In the absence of these cues, were more likely to impute nefarious motives to others and feel an unchecked anger towards them. So get out from behind your computer screen more often and interact with people in the real world as you do so, the general feeling that people are freakin terrible that can come from spending time online will often melt into, Folks aint so bad after all. Read more fiction. Studies show that reading fictional literature exercises the mental muscles that strengthen empathy. If youre looking for ideas on books to read, check out our mens fiction list. Imagine a different story about the people who annoy you. When you cut someone off while driving, you think to yourself, I hate to have done that but if I dont get to this interview on time, I wont get the job. But when someone else cuts you off, you think, What a complete asshole. We chalk our own misbehaviors up to circumstances, but blame the foibles of others on some inherent character flaw. Try offering the same compassion you give yourself to others by imagining possible reasons for why someone else might have done something rude or annoying. In my opinion, the best explanation of this exercise and how transformative it can be was given by author David Foster Wallace in a commencement address. Weve posted that excerpt in conjunction with this post, and strongly encourage you to take time to read it. Be curious about people. You cant get inside another persons shoes unless you really get to know them. Ask people clarifying questions so you can figure out where theyre coming from and understand what makes them tick. You can truly learn something about life and the human condition from every single person you meet. The more you develop your empathy, the more you realize that everybody has hard stuff in their life that theyre grappling with, and the more youll want to become an oasis for other people someone who lightens their burden by making them feel understood, safe, and rejuvenated even in the briefest of interactions. Conveying Warmth To Others. When you emanate Warmth people see you as being approachable, caring, and empathetic. When theyre around you they feel comfortable, understood, and taken care of. 
 How to Stop Linked. In App Notifications in Windows 1. Since Microsoft acquired Linked. In, Ive been dreading the day notifications to add someone Ive never met to my professional network pop up in my screen. Turns out that day is here, with Linked. In announcing its Windows 1. Luckily, you can change what apps demand your attention in the Windows 1. Microsoft Security Essentials Windows 7 Windows Defender Windows 8,Windows RT, Windows 8. 1, Windows RT 8. 1, Windows 10 Realtime protection against spyware. Torrentz domain names are for sale. Send an offer to contactinventoris. pl. Tabtight professional, free when you need it, VPN service. Windows downloads to help personalize and protect your PC. Nero Platinum combines dozens of programs in an ingenious package burn, copy, edit, stream, rip and convert. No one wants to buy a 500 hobby drone only to discover theyre a bad pilot, especially considering how one bad twist or crash can leave your investment in pieces. Action Center. If youre one of the brave who decide to install the Linked. In app, youre probably more plugged in than most to your career. But those updating blog post comments and friend requests are actually detrimental to getting work done. Distractions like notifications take you away from important tasks, and getting back on track after being interrupted takes a lot longer than you think. From your Windows 1. Start, then Settings the gear in the bottom left of your task bar. From there, hit System Notifications Actions to change which notifications you see. You can toggle notification banners and sounds, add or remove notifications from your PCs lock screen, or shut down all notifications to go distraction free. Nerds might want to take it a step further by getting rid of the Action Center altogether. It requires a bit of registry editing, something you shouldnt do unless youre well versed in Windows, but if youve got the guts to try it out then take a stab at it.
How to Stop Linked. In App Notifications in Windows 1. Since Microsoft acquired Linked. In, Ive been dreading the day notifications to add someone Ive never met to my professional network pop up in my screen. Turns out that day is here, with Linked. In announcing its Windows 1. Luckily, you can change what apps demand your attention in the Windows 1. Microsoft Security Essentials Windows 7 Windows Defender Windows 8,Windows RT, Windows 8. 1, Windows RT 8. 1, Windows 10 Realtime protection against spyware. Torrentz domain names are for sale. Send an offer to contactinventoris. pl. Tabtight professional, free when you need it, VPN service. Windows downloads to help personalize and protect your PC. Nero Platinum combines dozens of programs in an ingenious package burn, copy, edit, stream, rip and convert. No one wants to buy a 500 hobby drone only to discover theyre a bad pilot, especially considering how one bad twist or crash can leave your investment in pieces. Action Center. If youre one of the brave who decide to install the Linked. In app, youre probably more plugged in than most to your career. But those updating blog post comments and friend requests are actually detrimental to getting work done. Distractions like notifications take you away from important tasks, and getting back on track after being interrupted takes a lot longer than you think. From your Windows 1. Start, then Settings the gear in the bottom left of your task bar. From there, hit System Notifications Actions to change which notifications you see. You can toggle notification banners and sounds, add or remove notifications from your PCs lock screen, or shut down all notifications to go distraction free. Nerds might want to take it a step further by getting rid of the Action Center altogether. It requires a bit of registry editing, something you shouldnt do unless youre well versed in Windows, but if youve got the guts to try it out then take a stab at it. 
 The. NET Framework 4. NET Framework 4 is installed first. Both of these. NET Framework versions are no longer supported by Microsoft. NET Framework 4. You can install the. The most loved OS starts here. The Windows XP Commercial That Started Everything In 2001. Windows XP Professional ISO download for 32 bit and 64 bit pc. Windows XP Professional SP3 ISO bootable image free download. Windows XP is light, stable and super fast.
The. NET Framework 4. NET Framework 4 is installed first. Both of these. NET Framework versions are no longer supported by Microsoft. NET Framework 4. You can install the. The most loved OS starts here. The Windows XP Commercial That Started Everything In 2001. Windows XP Professional ISO download for 32 bit and 64 bit pc. Windows XP Professional SP3 ISO bootable image free download. Windows XP is light, stable and super fast.  NET Framework 4 on Windows XP. Its no longer supported by Microsoft. NET Framework 3. 5. You can install the. NET Framework 3. 5 on Windows XP.
NET Framework 4 on Windows XP. Its no longer supported by Microsoft. NET Framework 3. 5. You can install the. NET Framework 3. 5 on Windows XP.  The. NET Framework 3. NET Framework 1. 0 through 3. See also. Download the. NET Framework. Troubleshoot blocked. NET Framework installations and uninstallations. Install the. NET Framework for developers. Latest News. FSPs CMT510 Features Tempered Glass Galore Xilinix Pairs AMDs EPYC With Four FPGAs At Supercomputing 2017 Overclocking Returns To. DLL information of Windows XP Resources,Import,Export,Icons,Cursors, and more. Sorry, page not found Please enable cookies and refresh the page.
The. NET Framework 3. NET Framework 1. 0 through 3. See also. Download the. NET Framework. Troubleshoot blocked. NET Framework installations and uninstallations. Install the. NET Framework for developers. Latest News. FSPs CMT510 Features Tempered Glass Galore Xilinix Pairs AMDs EPYC With Four FPGAs At Supercomputing 2017 Overclocking Returns To. DLL information of Windows XP Resources,Import,Export,Icons,Cursors, and more. Sorry, page not found Please enable cookies and refresh the page. 
 Gmail is email thats intuitive, efficient, and useful. 15 GB of storage, less spam, and mobile access. InfoLIII 108 1 of 8 Rev. 11208 ASNT Certification Guide NDT Level III PdM Level III Certification Requirements ASNT NDT Level III certification is available. There is a large amount of Probability of Detection PoD data available eg National NDT Centre UK, NORTEST Norway, NIL Netherlands and in particular. Issuu is a digital publishing platform that makes it simple to publish magazines, catalogs, newspapers, books, and more online. Easily share your publications and get. International Journal of Engineering Research and Applications IJERA is an open access online peer reviewed international journal that publishes research. ENGINEERING HANDBOOK. Introduction. This book was created based on years of research and experience of G. L. Huyett staff and is intended to be a consolidated.
Gmail is email thats intuitive, efficient, and useful. 15 GB of storage, less spam, and mobile access. InfoLIII 108 1 of 8 Rev. 11208 ASNT Certification Guide NDT Level III PdM Level III Certification Requirements ASNT NDT Level III certification is available. There is a large amount of Probability of Detection PoD data available eg National NDT Centre UK, NORTEST Norway, NIL Netherlands and in particular. Issuu is a digital publishing platform that makes it simple to publish magazines, catalogs, newspapers, books, and more online. Easily share your publications and get. International Journal of Engineering Research and Applications IJERA is an open access online peer reviewed international journal that publishes research. ENGINEERING HANDBOOK. Introduction. This book was created based on years of research and experience of G. L. Huyett staff and is intended to be a consolidated. 
 It was the room where President Trump allegedly had two sex workers urinate on the bed as a sign of disrespect to Barack Obama, who had previously stayed in the same room. And the segment is pretty nerve racking. By now youve probably heard about the alleged Trump pee tape that was filmed by Russian spies in the Presidential Suite of the Ritz Carlton in Moscow. President Trump himself has insisted its not real, pointing out in his defense that hes very much a germaphobe. But as 2. Other bizarre stories in the so called Trump Dossier, first published by Buzzfeed, have since been confirmed. Colbert is the first American TV personality to film the room since Trump allegedly made it rain in 2. And without spoiling too much, Ill just say that the bed is the least interesting thing about the whole segment. Not only does Colbert give viewers a glimpse at the perspective from sitting in the bed youre looking right at the Kremlin he pulls a stunt that seems to get him in legitimate trouble with hotel security. Again, I wont spoil to much, but lets just say the idea that theres hidden surveillance going on in that room is more or less confirmed. That doesnt mean the pee tape is real, but given just how bizarre everything in Trumps orbit has been this year, its getting harder and harder to call the idea absurd. You.
It was the room where President Trump allegedly had two sex workers urinate on the bed as a sign of disrespect to Barack Obama, who had previously stayed in the same room. And the segment is pretty nerve racking. By now youve probably heard about the alleged Trump pee tape that was filmed by Russian spies in the Presidential Suite of the Ritz Carlton in Moscow. President Trump himself has insisted its not real, pointing out in his defense that hes very much a germaphobe. But as 2. Other bizarre stories in the so called Trump Dossier, first published by Buzzfeed, have since been confirmed. Colbert is the first American TV personality to film the room since Trump allegedly made it rain in 2. And without spoiling too much, Ill just say that the bed is the least interesting thing about the whole segment. Not only does Colbert give viewers a glimpse at the perspective from sitting in the bed youre looking right at the Kremlin he pulls a stunt that seems to get him in legitimate trouble with hotel security. Again, I wont spoil to much, but lets just say the idea that theres hidden surveillance going on in that room is more or less confirmed. That doesnt mean the pee tape is real, but given just how bizarre everything in Trumps orbit has been this year, its getting harder and harder to call the idea absurd. You. 
%2C445%2C286%2C400%2C400%2Carial%2C12%2C4%2C0%2C0%2C5_SCLZZZZZZZ_.jpg) Device Deluxe Edition CdParty feat. Andre 3. Rather Die Young. Start Over. 8 Love On Top. Countdown. 10 End of Time. I Was Here. 12 Run the World GirlsCD2 1 Lay Up Under Me. Schoolin Life. 3 Dance for You. Run the World Girls Kaskade Club Remix5 Run the World Girls Red. Top Club Remix6 Run the World Girls Jochen Simms Club RemixGnero R B, pop, soul. Longitud 4. 6 3. Etiqueta Parkwood, Columbia. Productor Antonio Dixon, Babyface, Brent Kutzle, Beyonc Knowles exec., Caleb, Jeff Bhasker, Napolitano Julian, Bergmark Jens, Kuk Harrell, Kanye West, Kaskade, Steele Lucas, Los Da Mystro, Ryan Tedder, Shea Taylor, conmutador, Symbolyc Uno, The Dream, Tricky Stewart. Beyonce 4 Deluxe Edition 2. CD2. CDs Genre Pop Release 2. Tracks 1. 8 M4. A Size 1. 53. 0. MBDescarga.
Device Deluxe Edition CdParty feat. Andre 3. Rather Die Young. Start Over. 8 Love On Top. Countdown. 10 End of Time. I Was Here. 12 Run the World GirlsCD2 1 Lay Up Under Me. Schoolin Life. 3 Dance for You. Run the World Girls Kaskade Club Remix5 Run the World Girls Red. Top Club Remix6 Run the World Girls Jochen Simms Club RemixGnero R B, pop, soul. Longitud 4. 6 3. Etiqueta Parkwood, Columbia. Productor Antonio Dixon, Babyface, Brent Kutzle, Beyonc Knowles exec., Caleb, Jeff Bhasker, Napolitano Julian, Bergmark Jens, Kuk Harrell, Kanye West, Kaskade, Steele Lucas, Los Da Mystro, Ryan Tedder, Shea Taylor, conmutador, Symbolyc Uno, The Dream, Tricky Stewart. Beyonce 4 Deluxe Edition 2. CD2. CDs Genre Pop Release 2. Tracks 1. 8 M4. A Size 1. 53. 0. MBDescarga.